BitLocker
On 24th September, Microsoft released a software update for Windows 10 (KB4516071) which modified the default behaviour of BitLocker.
BitLocker is the embedded full drive encryption technology built into Windows, offering protection against data loss if the physical hardware becomes compromised. I personally always enable BitLocker on portable Windows devices, as well as the equivalent full drive encryption technologies on macOS (Apple File Vault) and Linux.
Historically, where available, Windows would enable hardware-based encryption, which offers better performance than the software-based equivalent. For example, when buying a Samsung SSD, Samsung provides the option to enable hardware-based encryption using its own method, designed specifically for the drive itself.
Although more performant, this approach relies on the hardware provider to ensure the encryption method is secure. Unfortunately, security researchers have discovered that not all providers can be trusted, potentially putting the data at risk and voiding the value of full drive encryption.
As a result, Microsoft has made the decision to make software-based encryption the default for BitLocker moving forward (existing drives will not be changed).
Although I fully understand and respect the response from Microsoft (protecting the user should always be the first priority), it does mean that by default, anyone looking to leverage BitLocker will (by default) be sacrificing performance. When combined with the performance penalties associated with other vulnerabilities such as Meltdown and Spectre, this outcome is a little disappointing.
As an example, in the article “ThinkPad X1 Extreme”, I benchmarked (PCMark 10 Windows 10 without drive encryption. Following the new update form Microsoft, I enabled BitLocker and re-ran the benchmark. The results can be found below.
- BitLocker Disabled: 4716
- BitLocker Enabled (Software-Based): 4259
Although not completely scientific, the benchmark highlights a performance penalty of approximately 10%, which is in line with my expectation of software-based encryption.
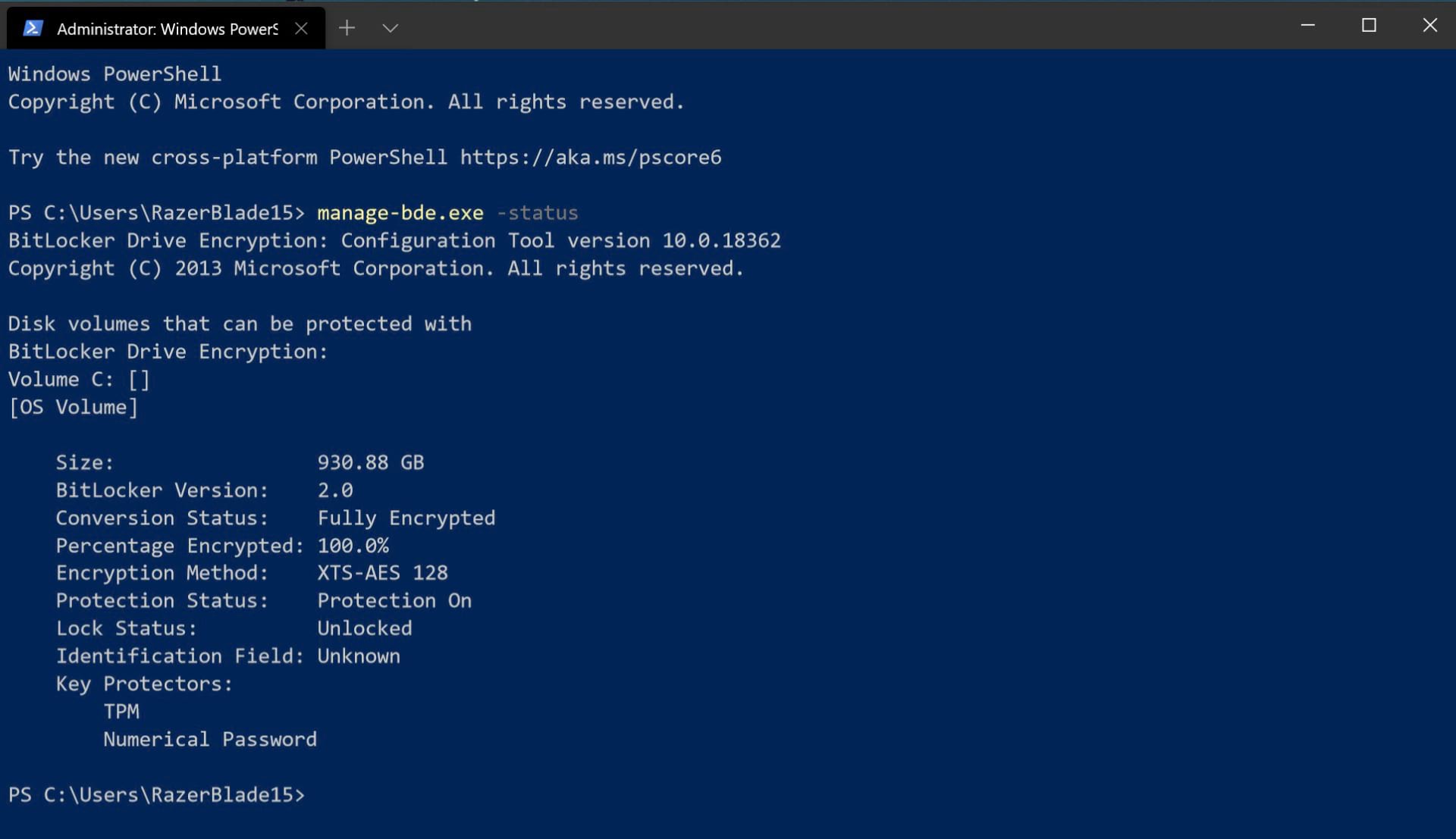
If you have enabled BitLocker, but unsure if hardware-based encryption has been enabled, simply run the following command as an administrator from the command line.
manage-bde.exe -status
If hardware-based encryption is enabled, it will be clearly stated as part of the read-out. For example, the image below does not specifically state hardware-encryption.
Finally, assuming you trust your hardware provider, it is possible to overwrite the default BitLocker setting. To achieve this outcome, I recommend referring to your hardware providers documentation, as the process may require third-party software. For example, Samsung drives can be managed using their “Samsung Magician” software.