Identity Access Management
This article is part of a series. I would recommend reading the articles in order, starting with “Modern IT Ecosystem”, which provides the required framing.
As a brief reminder, this series aims to explore the “art of the possible” if an enterprise business could hypothetically rebuild IT from the ground up, creating a modern IT ecosystem.
Within this article, I will highlight my proposed Identity Access Management (IAM) architecture, describing my philosophy, key technology decisions and positioning.
Introduction
As previously described, I have positioned a Zero Trust IT security model. Zero Trust is a holistic approach to IT security, which goes beyond the traditional “trust but verify” and “moat/castle” strategies. Although these traditional strategies are still common within enterprise businesses, they primarily target environments where the business has end-to-end ownership, management and control of all IT services.
In a modern IT ecosystem, it is very common for IT services to be distributed (e.g. SaaS Services, Cloud Hosting. etc.) Therefore, the users, services and data could be anywhere and everywhere, making the task of IT security increasingly complex.
The answer to this challenge is not to perpetuate the inadequate strategies (e.g. moat/castle), but instead look to implement a new strategy, where the network is always assumed to be hostile, meaning internal and external threats exist at all times.
With this in mind, Zero Trust implements new principles, techniques and technologies to help localise and isolate threats. For example, the following principles provide the foundation for a Zero Trust architecture.
-
The network is always assumed to be hostile, meaning external and internal threats exist on the network at all times.
-
Network locality (moat/castle) is not sufficient for deciding trust. No user or device is automatically trusted.
-
Micro-segmentation concepts create secure enclaves, limiting network and application flows between workloads, reducing the “blast radius” of an attack.
-
Every device, user and network flow is authenticated and authorised, preferably leveraging Multi-Factor Authentication (MFA).
-
A least-privilege access philosophy (need-to-known basis), where users are only granted the required access to complete their job (nothing more).
-
Policies must be dynamic and calculated from as many sources of data as possible, enabled via a central management control plane.
Enabling these principles requires new technologies and techniques, such as Modern Identity Access Management, Microcore, Segmentation and Deep Visibility, which aim to provide a structured approach to threat identification, as well as limiting the impact of a breach.
At the foundation, a Zero Trust architecture must be able to complete strict identity verification for every user and device trying to access a business resource, regardless of whether they exist within or outside of the network perimeter.
Therefore, from an IT security perspective, Identity Access Management (IAM) becomes one of the most important and powerful technologies used to protect the business.
Architecture
Identity Access Management (IAM) aims to define and manage the role and access privileges of a user (e.g. employees, contractors, customers) and the circumstances in which they would be granted (or denied) specific privileges.
The primary goal of Identity Access Management (IAM) is to create a single digital identity per user. Once that digital identity has been established, it must be maintained, modified and monitored throughout the user’s access lifecycle.
The diagram below outlines my proposed Identity Access Management (IAM) architecture, including the provisioning flows.
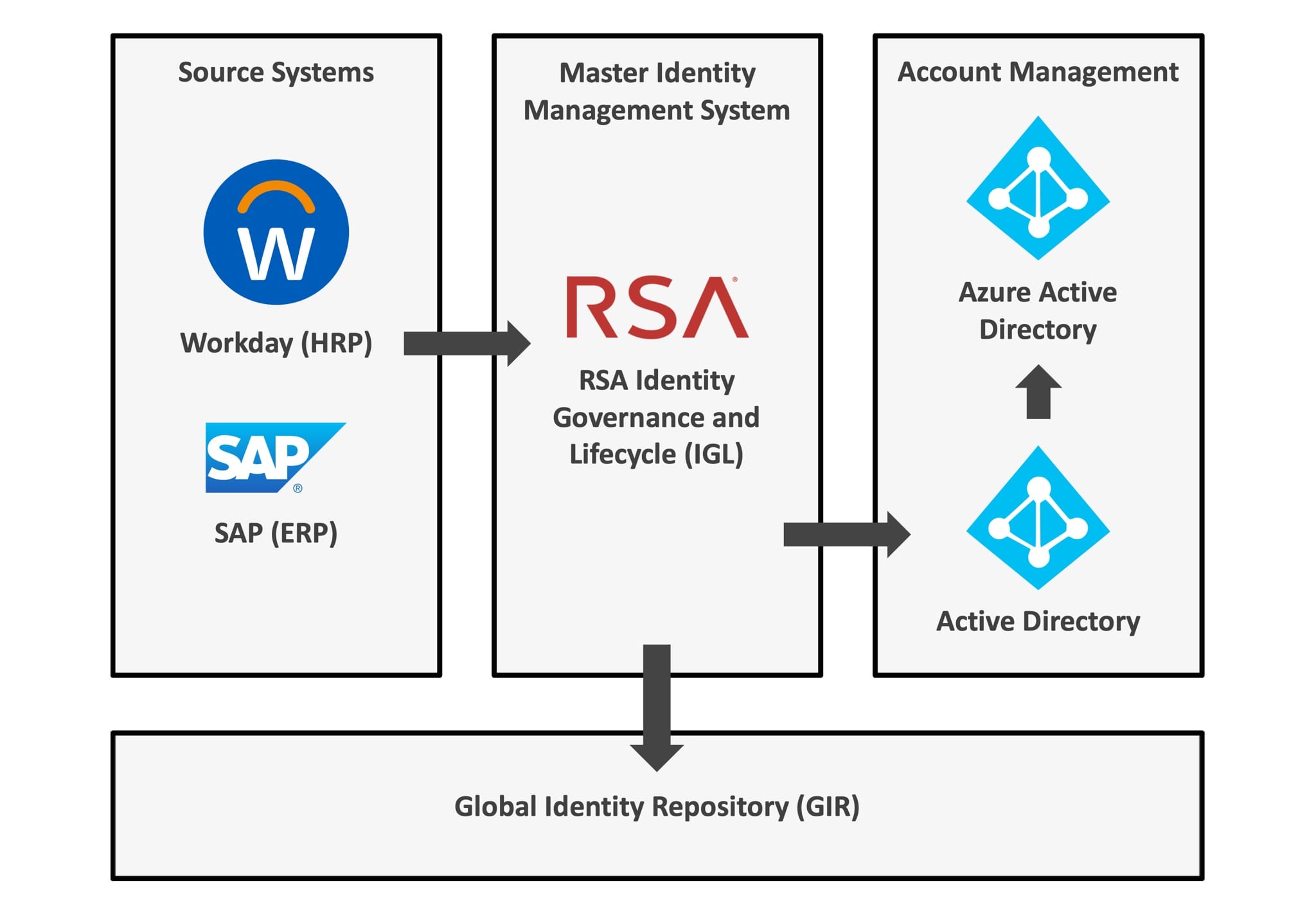
To enable this architecture, I would position the following technologies:
-
Workday, SAP: Multiple decoupled source systems (specifically HR and ERP) synchronise data with the Master Identity Management System, providing flexibility and agility, specifically covering mergers, acquisitions, divestitures, etc.
-
RSA Identity Governance Lifecycle (IGL): A unified Master Identity Management System, managing the lifecycle of identities, facilitating the Joiner/Mover/Leaver (JML) processes and providing continuous compliance capabilities.
-
Global Identity Repository: A connected data source, providing secure/scalable access to user data via a RESTful API.
-
Active Directory: Directory services, providing authentication and authorisation services for the Colocation Data Centres, Edge Computing and legacy federation.
-
Azure Active Directory: Directory services, providing authentication and authorisation services for applications in the cloud (SaaS, Public Cloud), as well as modern federation.
Positioning RSA (part of Dell Technologies) and Microsoft complements my Hybrid Multi-Cloud and Device-as-a-Service strategies, whilst also simplifying the Identity Access Management (IAM) architecture through capability consolidation. For example:
-
RSA IGL would focus on Access Certification, User Provisioning, Policy Automation and Role Management, whilst providing self-service capabilities and enterprise visibility across the access lifecycle.
-
Microsoft Active Directory and Azure Active Directory enable key authentication patterns, including SAML, OAuth 2.0, OpenID Connect, MAPI, WS-Federation, Kerberos, LDAP, etc.
As highlighted as part of my proposed Automation architecture, I have positioned ServiceNow for IT Service Management (ITSM). Although not depicted, ServiceNow would also facilitate identity processes, specifically request fulfilment and change control (approvals), as well as support any workflow automation requirements.
NOTE: I plan to cover my proposed IT Service Management architecture in a future article, which will include additional details regarding the positioning of ServiceNow.
Authentication Patterns
The diagram below outlines a range of authentication patterns, including their preference based on the proposed architecture.
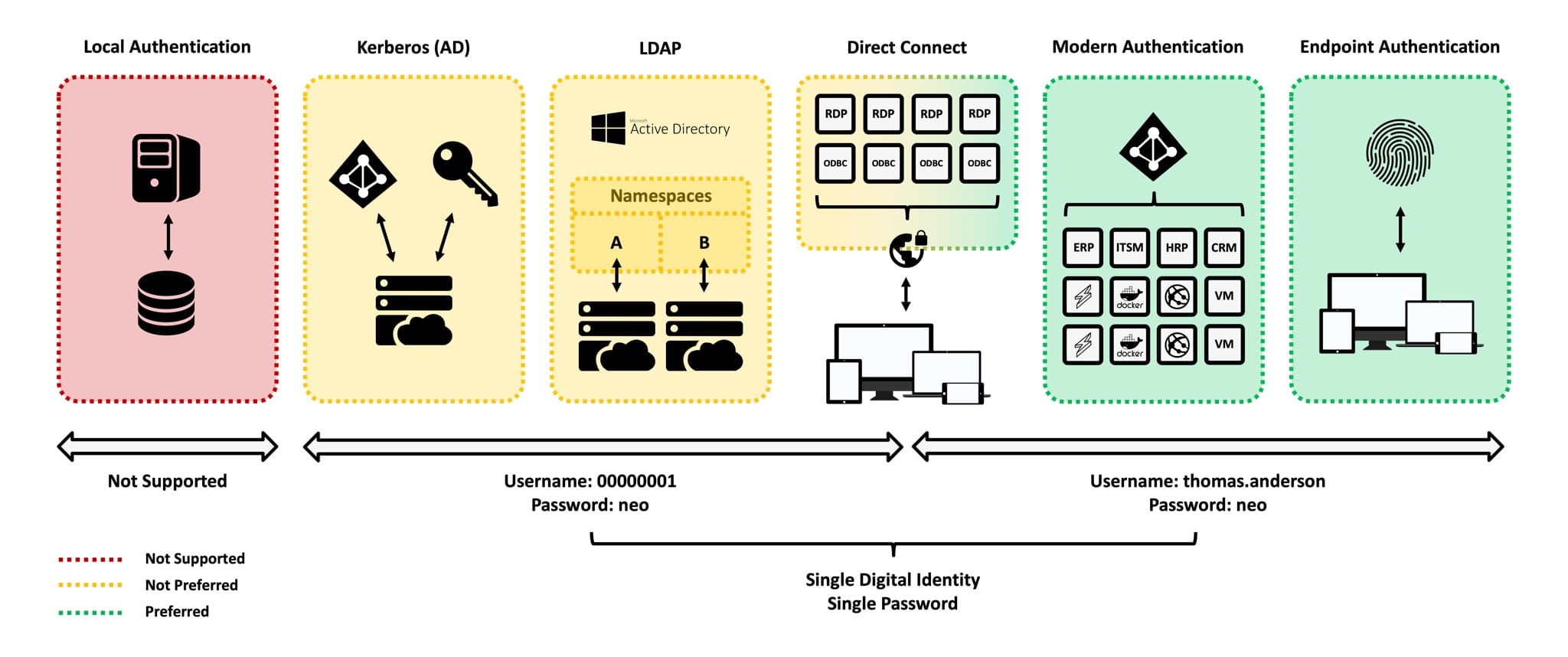
As you can see from the diagram, the user would have a single digital identity, with applications/services prioritising modern authentication.
With the previously defined business characteristics in mind, traditional authentication patterns cannot be completely ignored (specialist applications in R&D and Manufacturing). In these scenarios, the user would have a non-standard username, which would conform to the least common denominator (e.g. numbers only). In theory, through applications modernisation, these traditional authentication patterns would reduce over time.
-
Local Authentication: Local (decentralised) databases used for identity would not be supported within the ecosystem.
-
Kerberos: Kerberos is an authentication protocol that works based on tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. Kerberos would not be preferred, but technically viable within the proposed architecture.
-
LDAP: The Lightweight Directory Access Protocol (LDAP) is an open protocol for accessing and maintaining distributed directory information services over a network. Similar to Kerberos, LDAP would not be preferred, but technically viable within the proposed architecture.
-
Direct Connect: Specific services that require a direct connection, potentially via an insecure protocol. These services would not be directly accessible to the Internet and include an additional level of authentication before establishing a connection.
-
Modern Authentication: Modern Authentication leverages tokens, sent to an authentication provider. This removes the need for the username and password to be sent over the network. For example, SAML, OAuth 2.0, OpenID Connect, MAPI, WS-Federation, etc. Preferred for all applications and services.
-
Endpoint Authentication: Aligned with “Modern Authentication”, enabling password-less authentication via a gesture (e.g. facial recognition, iris scan, fingerprint, etc.) Preferred for all endpoints (clients/mobiles).
My holistic vision would be to enable a password-less ecosystem, where modern authentication patterns would be utilised by all applications, services and endpoints.
Thanks to my positioning of Microsoft Windows 10 and Apple iOS (Clients/Mobiles), password-less could be enabled by default, leveraging technologies such as Windows Hello and Apple Face ID/Touch ID.
Windows Hello is compatible with any service that supports Fast Identity Online (FIDO). Therefore, as Windows Hello matures, the use of password-less would increase over time.
Conclusion
In conclusion, I feel strongly that any modern IT ecosystem must target a Zero Trust IT security model, where Identity Access Management (IAM) would play a critical role.
This approach would help to ensure the ecosystem is protected, without limiting the ability to innovate and leverage cutting-edge technologies. The option to enable password-less authentication for the majority of use cases would be an exciting prospect, recognising that IT can rarely improve security and the user experience at the same time.