Device-as-a-Service
This article is part of a series. I would recommend reading the articles in order, starting with “Modern IT Ecosystem”, which provides the required framing.
As a brief reminder, this series aims to explore the “art of the possible” if an enterprise business could hypothetically rebuild IT from the ground up, creating a modern IT ecosystem.
Within this article, I will highlight my proposed Device-as-a-Service (endpoint) architecture, describing my philosophy, key technology decisions and positioning.
Introduction
As described in the article “Modern IT Ecosystem”, I have positioned a Zero Trust security model, which aims to localise and isolate threats through microcore, segmentation and deep visibility.
This model also extends to the endpoints (e.g. desktops, laptops, tablets, smartphones), which I would treat as a commodity (untrusted). To enable this outcome, the enterprise security controls would be layered throughout the end-to-end ecosystem, with solutions being secure by design (secured at the source), whilst complemented by a robust Identity Access Management architecture and a clear “least privilege access” strategy.
As a result, my proposed endpoint architecture would prioritise productivity, delivering a “consumer-like” experience.
For example, enterprise endpoints are commonly overloaded with third-party security software, generally resulting in multiple running agents. These agents continuously consume system resources (processor and memory), as well as often require kernel-level access, which (ironically) opens a high-risk attack vector.
As an alternative, I would leverage the native capabilities of the specific device (no third-party software), looking to embrace the embedded security mechanisms and controls. Not only would this dramatically simplify the architecture, but it would also improve the end-user experience, making it comparable to a consumer purchase from Dell, Apple, etc.
This approach also supports my goal of making the ecosystem device-agnostic, where any endpoint (e.g. Windows, macOS, Linux, ChromeOS, iOS Android) could be utilised with minimum effort. I feel this would be an important architecture tenant, recognising the rapid growth of connected devices (e.g. Sensors) and new forms of Human-Computer Interaction (e.g. Mixed Reality Headsets).
Considering this security model and device-agnostic strategy, you might assume that I would position “Bring Your Own Device (BYOD)”. Over the past decade, BYOD has become a popular trend, however, the true value is often reduced/lost due to the inherent complexities regarding security, privacy and local law. As a result, many respected analysts have rebranded BYOD as “Bring Your Own Disaster”.
Therefore, I would position a “Choose Your Own Device (CYOD)” strategy, where the enterprise retains ownership of the device itself (clear separation between personal and business), but still provides flexibility for users to personalise their experience.
Device-as-a-Service
As previously stated, I see the endpoint as a commodity. As a result, I would treat the processes (e.g. provisioning, lifecycle, break-fix) supporting the endpoint “as-a-Service”. The “as-a-Service” paradigm is well established with software (e.g. SaaS, Public Cloud), but is more complex when physical hardware is involved.
Thankfully, the major personal computer providers (e.g. Dell, Lenovo) all offer Device-as-a-Service and/or PC-as-a-Service capabilities, where they aim to combine hardware, software, lifecycle, break-fix and financing as one all-encompassing service.
In this scenario, the business simply provides the required specification (e.g. hardware, software) and configuration (e.g. settings, policies), with all other logistics being managed by the personal computer provider. The high-level diagram below outlines the process.
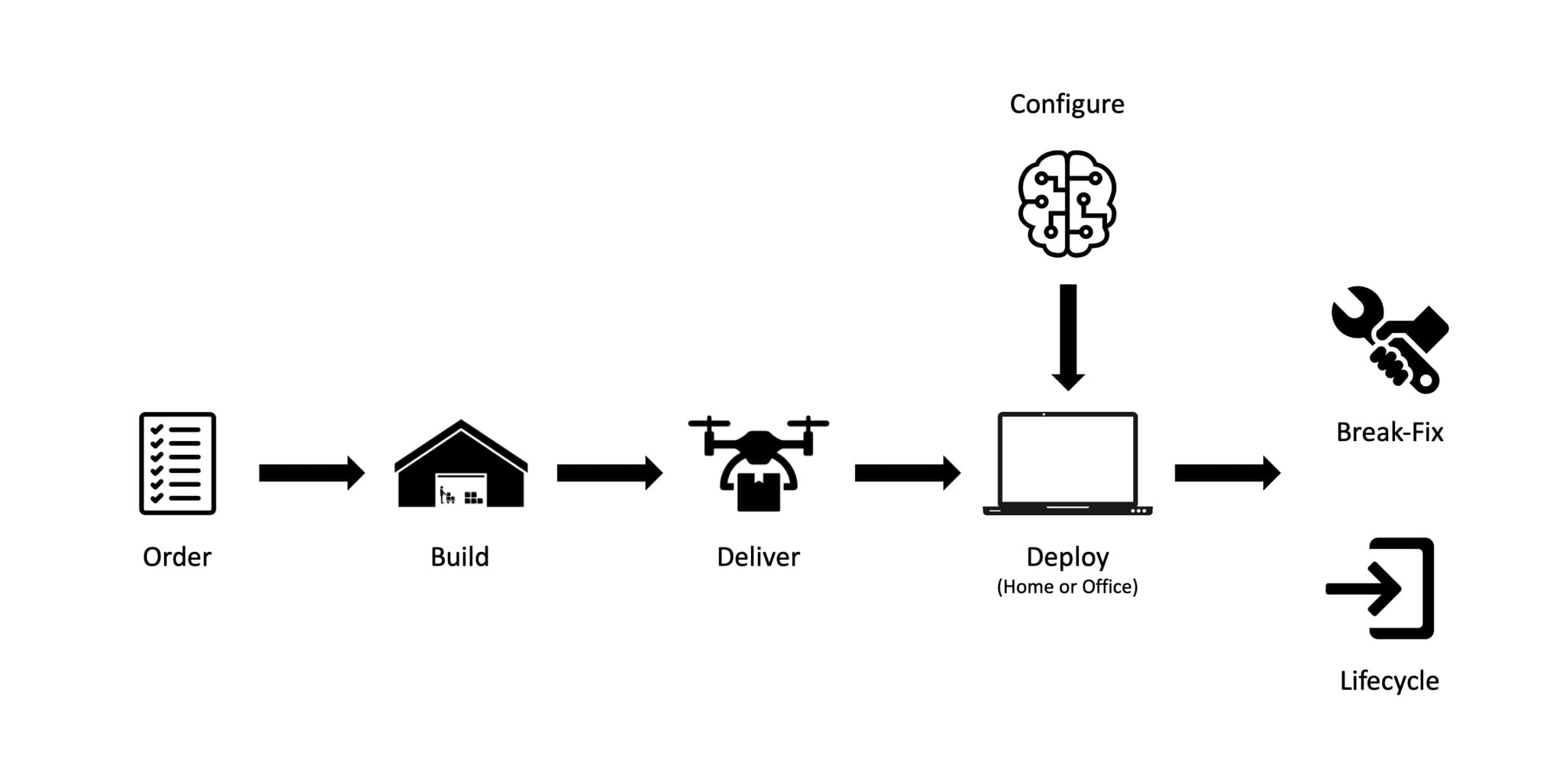
A key enabler of this process would be the ability to configure the builds at the point of use. Historically, enterprise businesses would have to create and maintain a build (image), which would include a specific version of the operating system, as well as all base drivers, configuration and software. The provisioning and maintenance of this build (or builds) could be frustratingly complex, as well as resource-intensive and time-consuming.
With Windows 10, Microsoft introduced a new capability known as Windows Autopilot, which removes the need to manage a traditional build, allowing devices to be automatically configured upon delivery.
Windows Autopilot
Windows Autopilot is a capability designed to pre-configure, provision, repurpose and recover devices. I would position the use of Windows AutoPiot, looking to simplify my end-to-end device lifecycle management process, supported by a certified personal computer provider.
Windows Autopilot uses an OEM-optimised version of Windows 10, which comes pre-installed on the device. This removes the need for the enterprise to create and maintain a custom build (image).
At the point of deployment, instead of re-imaging the device, the OEM-optimised version of Windows 10 is transformed into a “business-ready” state. This includes the required configuration (e.g. settings, policies) and software (e.g. Office 365, Chrome).
Post-deployment, Windows Autopilot could be used to re-purpose the device by leveraging “Windows Autopilot Reset” or to support break-fix events.
As the name suggests, Windows Autopilot is a Windows-only feature (targeting Windows 10). However, recognising the framing of this series, I have assumed that 98% of the endpoints would be running Windows 10, with the remaining devices using a combination of macOS (1%) and a variant of Linux (1%).
Microsoft Intune, SCCM and JAMF
Microsoft Intune is a unified endpoint management solution, covering Windows, macOS, iOS and Android. I would position Intune as my primary endpoint management solution, used to automate provisioning, policy management, application delivery and updates.
Unfortunately, Intune is not yet feature-complete, especially when targeting legacy operating systems, as well as macOS and Linux. To ensure end-to-end compatibility, Microsoft System Center Configuration Manager (SCCM) and JAMF Pro would be positioned to compliment Intune.
Across the ecosystem, the use of SCCM and JAMF should be very limited (less than 5%). As Intune matures, the reliance on SCCM and JAMF should reduce further.
Hardware Architecture
As previously stated, I would target a “Choose Your Own Device (CYOD)” strategy, positioning Dell as my Autopilot certified personal computer provider for Device-as-a-Service (maximising the investments made as part of the Colocation Data Centre architecture).
To simplify the deployment of hardware, I would leverage a set of user personas (e.g. Office, Sales Representative, etc.) Each persona would be assigned default hardware; however, users would have the option to update their hardware selection to better support their business requirements.
Based on the current Dell range, I would position the following hardware, which would obviously evolve overtime:
Business Laptop
- Dell Latitude 5400
- 14” 1920x1080 Non-Touch Display
- 1.6GHz 4-Core Intel Core i5-8365U (Turbo 4.1GHz)
- 16GB DDR4 RAM
- 256GB M.2 PCIe NVMe SSD
- Intel UHD Graphics 620
- Intel Dual Band (802.11ac) Wireless + Bluetooth 5.0
- TPM 2.0 + Windows Hello
2-in-1 Laptop
- Dell Latitude 7400
- 12.3”/14” 1920x1280/1920x1080 Touch Display
- 1.6GHz 4-Core Intel Core i5-8365U (Turbo 4.1GHz)
- 16GB DDR4 RAM
- 512GB/512GB M.2 PCIe NVMe SSD
- Intel UHD Graphics 620
- Intel Dual Band (802.11ac) Wireless + Bluetooth 5.0
- TPM 2.0 + Windows Hello
High-Performance Laptop
- Dell Precision 5540
- 15” 1920x1080 100% sRGB Non-Touch Display
- 2.6GHz 6-Core Intel Core i7-9850H (Turbo 4.6GHz)
- 32GB DDR4 RAM
- 512GB M.2 PCIe NVMe SSD
- Intel UHD Graphics 630
- NVIDIA Quadro T1000 4GB GDDR5 (ISV Certified)
- Intel Dual Band (802.11ac) Wireless + Bluetooth 5.0
- TPM 2.0 + Windows Hello
Apple Mac
- Apple MacBook Pro
- 13” 2560×1600 P3 Colour Space Non-Touch Display
- 2.4GHz 4-Core Intel Core i5-8279U (Turbo 4.1GHz)
- 16GB DDR4 RAM
- 256GB NVMe SSD
- Intel Iris Plus Graphics 655
- 802.11ac Wireless + Bluetooth 5.0
- Apple T2 + Touch ID
All devices come with a minimum 1920x1080 resolution display, 16GB RAM, NVMe SSD, as well as hardware security and biometric authentication. This would provide a very strong foundation, delivering performance, sustainability and security across the entire range. The positioned High-Performance laptop also includes ISV certified graphics (NVIDIA Quadro T1000), providing support for specialist workloads.
Alongside the laptop range, I would also position two desktop computers (Dell Optiplex 3070 micro and Precision Workstation 3431). The use of desktop computers would be limited, but likely still a requirement for certain user personas. The Precision Workstation 3431 comes equipped with a Xeon Processor, ECC RAM and NVIDIA Quadro Graphics (ISV Certified), making it a very versatile computer, that could support the most demanding workloads.
Finally, regarding mobility, I would position the Apple iPhone and Apple iPad Air. At this time, I would not position Google Android as a standard mobile offering, however, this might change as the market matures.
Software Architecture
As a result of the previously defined security approach (leveraging the native capabilities of the specific device), the initial client software configuration would be incredibly simple.
Windows Desktop/Laptop
- Microsoft Windows 10 Enterprise 1903 (AKA 19H1)
- Microsoft Office 365 (Word, PowerPoint, Excel, Outlook, Teams)
- Google Chrome
- Palo Alto Networks Prisma Access
Apple Mac
- Apple macOS 10.15.1 (Catalina)
- Microsoft Office 365 (Word, PowerPoint, Excel, Outlook, Teams)
- Google Chrome
- Palo Alto Networks Prisma Access
With Microsoft releasing two major operating systems updates per year, I would aim to remain one version (six months) behind the current build (e.g. 1903 vs. 1909). This would help ensure the business remains current but also protected against unforeseen bugs via a short stabilisation period. The same philosophy would be applied to macOS, waiting for the release of 10.x.1, etc.
As per the previous defined IT principles and IT declarations, the majority of applications and services should be cloud-hosted (SaaS, Public Cloud), accessible over the Internet, via a browser or an API. I would position Google Chrome as the default browser, complimented by Microsoft Edge (Chromium Edition). Any traditional application that requires installation would be downloaded via the web or through Intune.
Only specialised applications running in a Colocation Data Centre would require direct network connectivity via the LAN/WLAN or client VPN. This is where Palo Alto Networks Prisma Access would be utilised to provide full-tunnel encryption.
NOTE: I plan to cover my proposed security architecture in a future article, which will include additional details regarding the use of Palo Alto Networks.
Conclusion
In conclusion, it is exciting to be able to propose an endpoint architecture that would prioritise productivity and user experience, whilst maintaining high standards regarding Information Security, Privacy and Quality. This is a rare combination, which demonstrates the value proposition of a modern IT ecosystem, helping to empower users, optimise operations and improve business agility.