Microsoft Account Alias
I registered for my primary email address in 2006 (16 years ago). Since that date, it has been used as the username for countless online accounts.
With hindsight, I would have used a custom domain (something that I own/manage) or created a unique username for each online account using a password manager, such as Bitwarden, etc.
However, in 2006 (I was at University), cybersecurity and online privacy were not high on my priority list.
Therefore, my email address is widely known, having been shared publically thousands of times, either via legitimate channels (with consent) or through one of the many cybersecurity breaches that have occurred during this time horizon.
For example, the website Have I Been Pwned can check to see if your email address has been leaked as part of a known data breach.
Thankfully, modern identity capabilities, such as Multi-Factor Authentication (MFA) and Conditional Access help to mitigate any immediate security concern.
With that said, these identity capabilities will not stop a cyber adversary attempting to gain access to your online accounts via a Brute-force Attack, MFA Fatigue and/or Social Engineering.
A recent example is my Microsoft Account. Looking at my “Sign-in Activity”, I can see my account is under continuous attack.
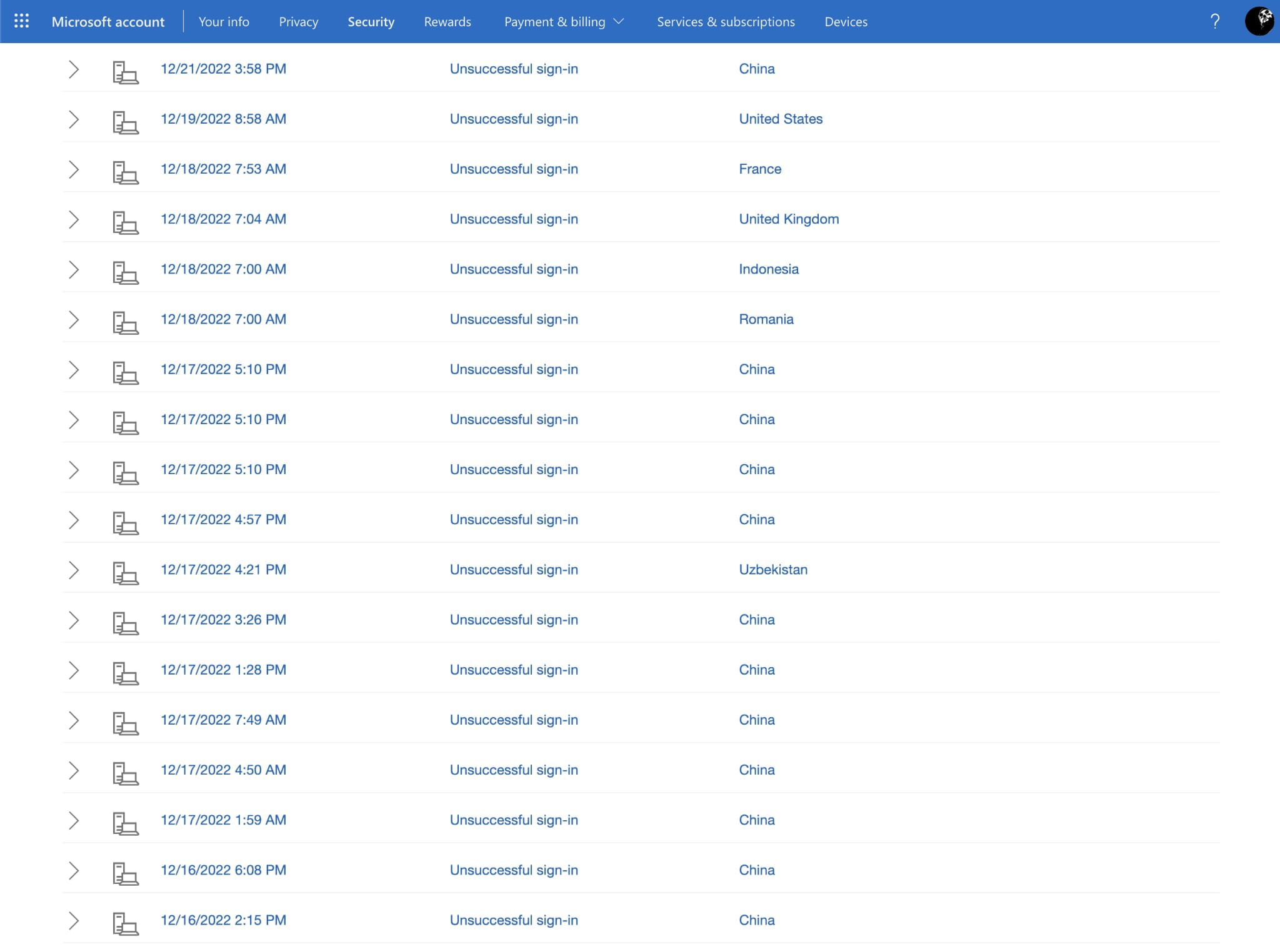
Thousands of sign-in attempts from unknown source IP addresses, usually via the web, but also using synchronisation options offered by Microsoft (Exchange ActiveSync, etc.)
Although the location field highlights attempts from around the world, the actual origin of the attack will likely never be known, as a cyber adversary will use a range of techniques to obfuscate their true location.
To check your Microsoft Account sign-in activity, navigate to:
My Microsoft Account > Security > Sign-in Activity
As previously stated, good security hygiene and the use of modern identity capabilities will help to ensure the account remains secure. However, this level of continuous attack is a little unsettling.
Therefore, if you find yourself in this position, I recommend considering a change of username (AKA Microsoft Account Alias). Unlike Apple and others, Microsoft makes this process fairly painless and it should immediately remove the risk associated with the original username.
Sign in to your Microsoft account and navigate to:
My Microsoft Account > Your Info > Edit Account Information > Account Alias
Here you can add a new account alias (email address). Where possible, I recommend using a secure and privacy-centric email service (like Proton Mail), configured with Multi-Factor Authentication (MFA) and a custom domain.
Once configured (and verified), you can set the new account alias as the primary and (if desired), remove the old account alias. The addition of an account alias may take 24 hours to propagate across all Microsoft services.
Finally, select “Change Sign-in Preferences” and ensure only your new primary account alias is enabled as a sign-in option.
Your account should now be secure, successfully removing the risk associated with the original username. As an additional step, I would also recommend signing out of all existing sessions. To do this, navigate to:
My Microsoft Account > Security > Advanced Security Options
At this point, you should be able to select “Sign Me Out”. This process may take 24 hours to complete across all active sessions.