Bromium
Over the past week I have been touring Silicon Valley with the Leading Edge Forum speaking with a number of technology companies.
One person that I spoke with was Simon Crosby, who is co-founder and CTO of Bromium. Simon has an impressive resume, having worked at Intel, co-founded XenSource and later acting as CTO at Citrix.
His latest venture with Bromium is focused on end-point security and I believe he may be on the verge of revolutionising the industry (again).
The Bromium premise is that client security is fundamentally flawed, as traditional anti-malware techniques are reactive, not proactive, and therefore can never be 100% effective. As a result they have changed the paradigm by developing a solution that enables end-points to protect themselves without requiring signatures or updates.
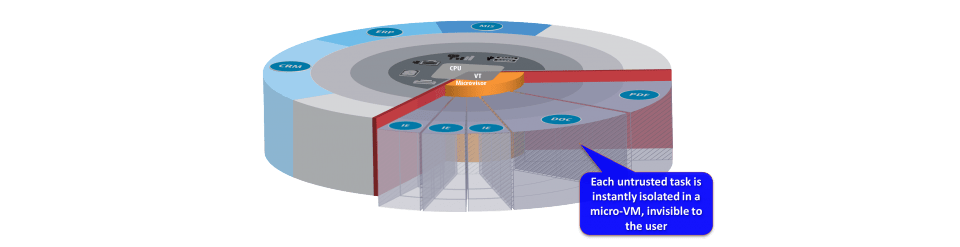
The solution itself is known as vSentry and is built on the Bromium Microvisor which is a Xen-based, security-focused hypervisor designed to automatically and invisibly hardware-isolate each vulnerable or untrusted user task.
For example, when the user starts a new task (e.g. opens a browser tab) the Microvisor instantly creates a new micro-VM in hardware. Any malware entering a micro-VM cannot modify the operating system or gain access to any data or network infrastructure. Therefore enabling proactive security and safety for the end-point.
If the user task requires access to files, networks, devices or the clipboard, the hardware interrupts execution and passes control to the Microvisor, which applies task-specific policies on a strictly “need-to-know” basis, ensuring security is maintained.
The diagram below highlights the Microvisor / micro-VM approach:
In my opinion this is the future of end-point security, where hardware-enforced isolation is used to stop previously undetectable attacks without disrupting the user experience. Unlike traditional security methods, this approach could deliver a 100% secure environment, covering all potential vulnerabilities.
The main issue with this approach is legacy infrastructure, as a system running vSentry could still infect non-vSentry end-points. Therefore at least in the short term users will likely require traditional malware protection to ensure total coverage of their environment.
Bromium vSenetry is currently available for Windows 7/8 and OS X, running Intel hardware (leveraging Intel VT technology). However it is also being tested for AMD and ARM processors and other operating systems such as Linux and Android.