Identity Services Engine
Identity Services Engine (ISE) is part of Cisco’s Borderless Network Architecture and is an evolution of the Cisco security product range. More specifically it consolidates existing products and services, such as NAC and ACS into one unified platform. The video below provides a brief overview:
At a high level ISE can be considered an evolution of NAC (Network Access Control), however in my opinion it is much more than that. It includes many new features beyond secure device access, such as on-boarding and policy control, as well as full end point visibility (of every device on your network). It even enables end point posture assessment and seamlessly integrates with the major MDM vendors (such as MobileIron).
Even with this high level understanding, the possibilities of ISE become clear and with the BYOD craze in full swing, it’s been perfectly timed by Cisco. To backup my thoughts, in the past month Gartner released a research document (Lawrence Orans & John Pescatore) stating that:
“The bring your own device (BYOD) phenomenon, in which employees are being allowed to use their own personal devices for business purposes, will lead to a revival of NAC. We believe NAC will emerge as one of the key mechanisms for providing a flexible approach to protecting the network against the risks of personally owned mobile devices.”
This statement is reinforced by their most recent Network Access Control Magic Quadrant, which positions Cisco and ISE as the market leader (just edging out Juniper).
Testing Identity Services Engine
Over the past few months I have been testing ISE and have now collected enough data to start sharing the output. I will aim to provide an overview of the setup, outline the test plan, as well as demonstrate the service in action. This article will start by outlining the test lab design.
The aim of the lab setup was to replicate a real world environment, including Active Directory and Certificate Services, as well as wired and wireless access. A high level design diagram can be found below (click to expand):
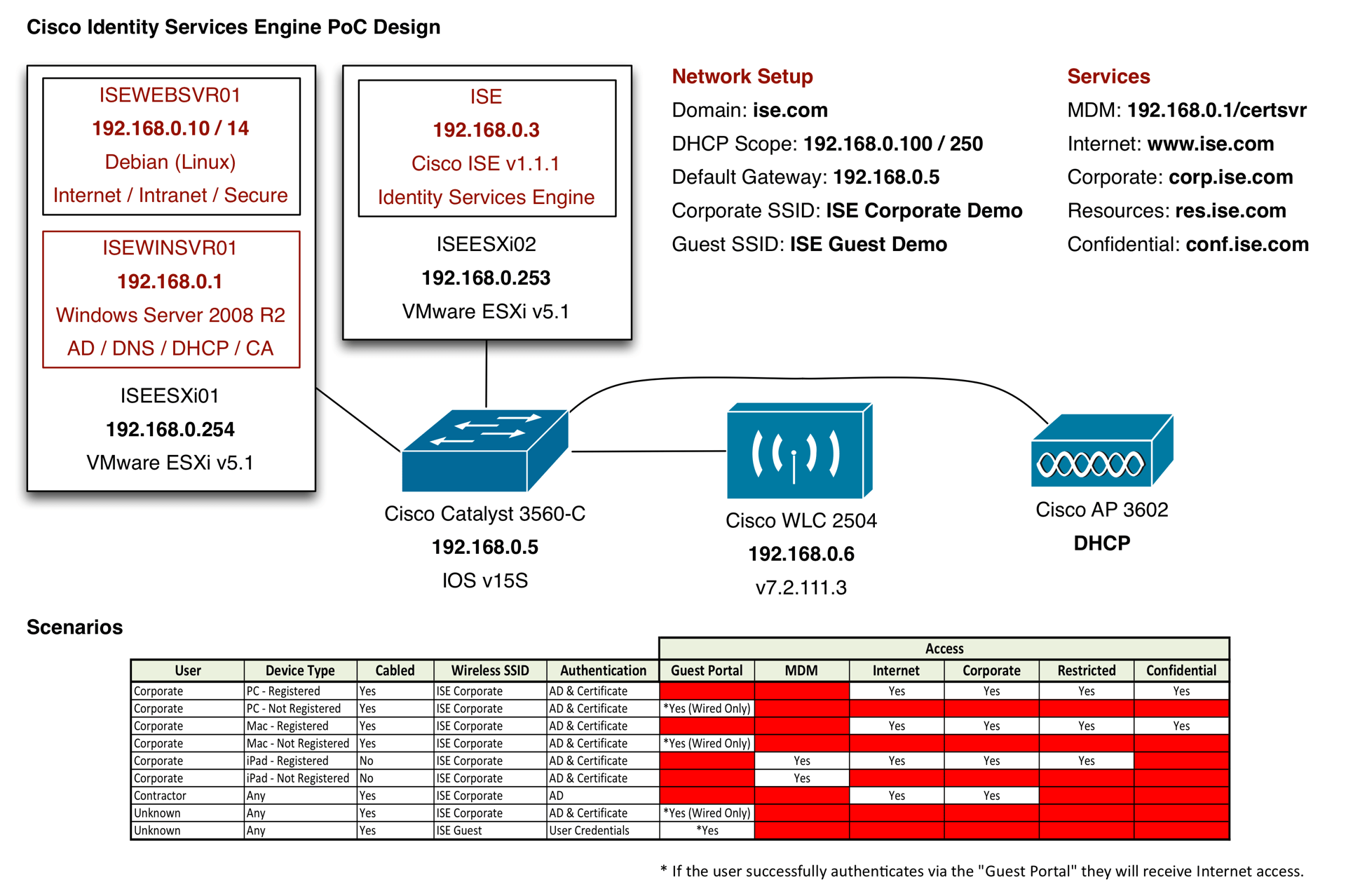
As you can see from the design, the majority of the environment is virtualised using VMware vSphere (ESXi v5.1). This type of configuration enables a quicker, simpler and cheaper setup by consolidating services (you can even use evaluation licences).
The first ESXi box includes two virtual machines, the first is a standard Windows Server (2008 R2 x64) and will act as our AD, DNS, DHCP and CA. In a real world environment it is likely that this services would be split out, however consolidated will be fine for this small scale lab. The second virtual machine is a simple Linux web server which will replicate network resources. For example, I have configured four web sites (individual IP addresses) that are called:
- Internet - Replicating the Internet
- Corporate - Replicating the Corporate Intranet
- Resources - Replicating higher security resources (HR, etc)
- Confidential - Replicating confidential resources
These web sites will be used to test and confirm different levels of access (depending on the user and/or device type).
The rest of the network setup is very simple, with a standard Catalyst switch which will be used to interconnect the devices, as well as for cabled access and a small wireless controller and access point which will broadcast two wireless networks:
- ISE Corporate Demo - Corporate SSID
- ISE Guest Demo - Guest SSID
Finally, ISE will also be running in a virtual machine, which is fully supported by Cisco and can be downloaded from their website (Cisco account required).
The other important part of the design are the scenarios that will be configured. As you can see from the design document, I have outlined the the user, device type, authentication method and level of access granted. This includes both registered and non-registered devices. The aim is to test different users, device types and automatic on-boarding (provisioning) via wired and wireless (single Corporate SSID). Therefore showing the different levels of security and control that can be achieved using ISE.
This concludes the ISE test lab design and deliverers (with as little as four devices) a standalone environment that replicates a business network. This environment can now be used to safely test and demonstrate the many different capabilities of ISE.