Web Proxy Autodiscovery
I have previously written about how you can use a proxy auto-config (PAC) file to direct your web users to an appropriate proxy server for fetching a given URL. Unfortunately you still have to tell the client’s browser how to access that file and if you support several thousand users this configuration process can be a bit of a nightmare. One option is to hardcode the PAC files URL into the browser, however this can make any future infrastructure changes difficult and also provides little resilience if the PAC file becomes unavailable. It also offers no compatibility if the user was to connect from outside the corporate network. This is especially frustrating for roaming users who often need to connect to wireless hotspots that require web authentication. In this case the user would need to make a modification to the browser configuration, which although is relatively simple, is not recommended for enterprise level support.
The Web Proxy Autodiscovery Protocol (WPAD) is a method used by browsers to automatically locate a proxy auto-config file. When WPAD is used the .pac extension is updated to wpad.dat, however the file content is exactly the same as a PAC file.
WPAD was created by Microsoft and has been supported since Internet Explorer 5.0.
The WPAD standard dictates two methods in which the IT administrator can publish the location of the PAC file, using the Dynamic Host Configuration Protocol (DHCP), the Domain Name System (DNS) or both.
When the user first opens their browser to navigate to a web page, there will be a few seconds delay. It is during this time that the browser is automatically detecting the proxy settings. First, it checks the information received from the DHCP server, looking for site-local option 252, auto-proxy-config, which should include a string value http://xxx.xxx.xxx.xxx/wpad.dat where xxx.xxx.xxx.xxx is the address of a web server (IP or DNS).
If the DHCP server does not provide the information, DNS will be used. The browser requests from the DNS server to identify the IP address for WPAD. For example, if the network name of the user’s computer is pc.branch.region.company.com, the browser will automatically try the following URLs in turn until it finds a proxy configuration file:
- http://wpad.branch.region.company.com/wpad.dat
- http://wpad.region.company.com/wpad.dat
- http://wpad.company.com/wpad.dat
- http://wpad.com/wpad.dat
For DNS lookup the file must be named wpad.dat and be located in the WPAD web site’s root directory.
Whether DHCP or DNS is used, the web server must be configured to set up dat files with a MIME type of application/x-ns-proxy-autoconfig. Although for DNS lookups, the path of the configuration file must always be wpad.dat, for the DHCP protocol, any URL is usable. Finally because DHCP has a higher priority than DNS, if DHCP provides the WPAD URL, no DNS lookup is completed.
When located, the browser will download the auto proxy-config file through the HTTP protocol and configure itself according to the content of the file.
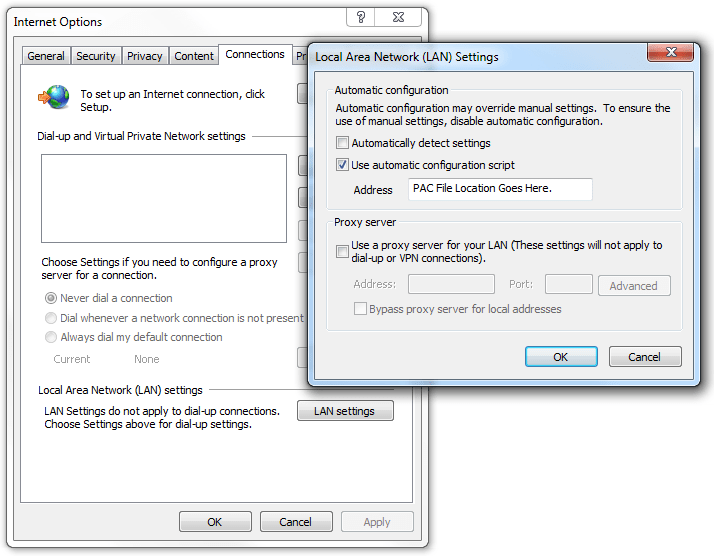
On the client side the only configuration that needs to take place is to tick the Automatically Detect Settings option in Internet Options > Connections > LAN Settings. This option is enabled by default in Internet Explorer or can be enabled via domain Group Policy. By having just this simple option enabled the client’s browser should be able to handle any network configuration automatically, whether they are connected to the corporate LAN, at home, or to a wireless hotspot.
Security Concerns:
Although WPAD greatly simplifies browser proxy configuration, it does have to be handled with care. Two specific examples of where WPAD can be used in a maliciously fashion are:
-
A rogue DHCP server is added to a network that starts issuing a non-approved PAC file. This could result in your users traffic and browsing information being forwarded to an untrustworthy source.
-
When using DNS lookup, if your company uses the domain
branch.company.comand the PAC filehttp://wpad.branch.company.com/wpad.datis not successfully served, the browser will automatically attempt to locate the file athttp://wpad.company.com/wpad.datand thenhttp://wpad.com/wpad.dat. It is possible that an attacker could configure and deliver a malicious PAC file from one of these un-approved locations.